
Since the internet’s earliest days, public-facing organizations have established security systems to defend sensitive data from external forces that seek to compromise it. One tried-and-true method is the creation of sub-networks between untrusted WANs and an organization’s internal resources, dubbed demilitarized zones (DMZ).
Though DMZ networks still offer a buffer between untrusted users and internal segments, the adoption of cloud services and virtualization means the in-house hosting of web servers isn’t as necessary. While DMZ networks get phased out, zero trust network architectures (ZTNA) remain a popular framework in cybersecurity.
Are DMZ networks enough in an ever-evolving digital ecosystem, or is zero trust more worthy of consideration? This article looks at demilitarized zones and zero trust networks, how they differ, and whether DMZ frameworks are still viable security components.
What Is a DMZ Network?
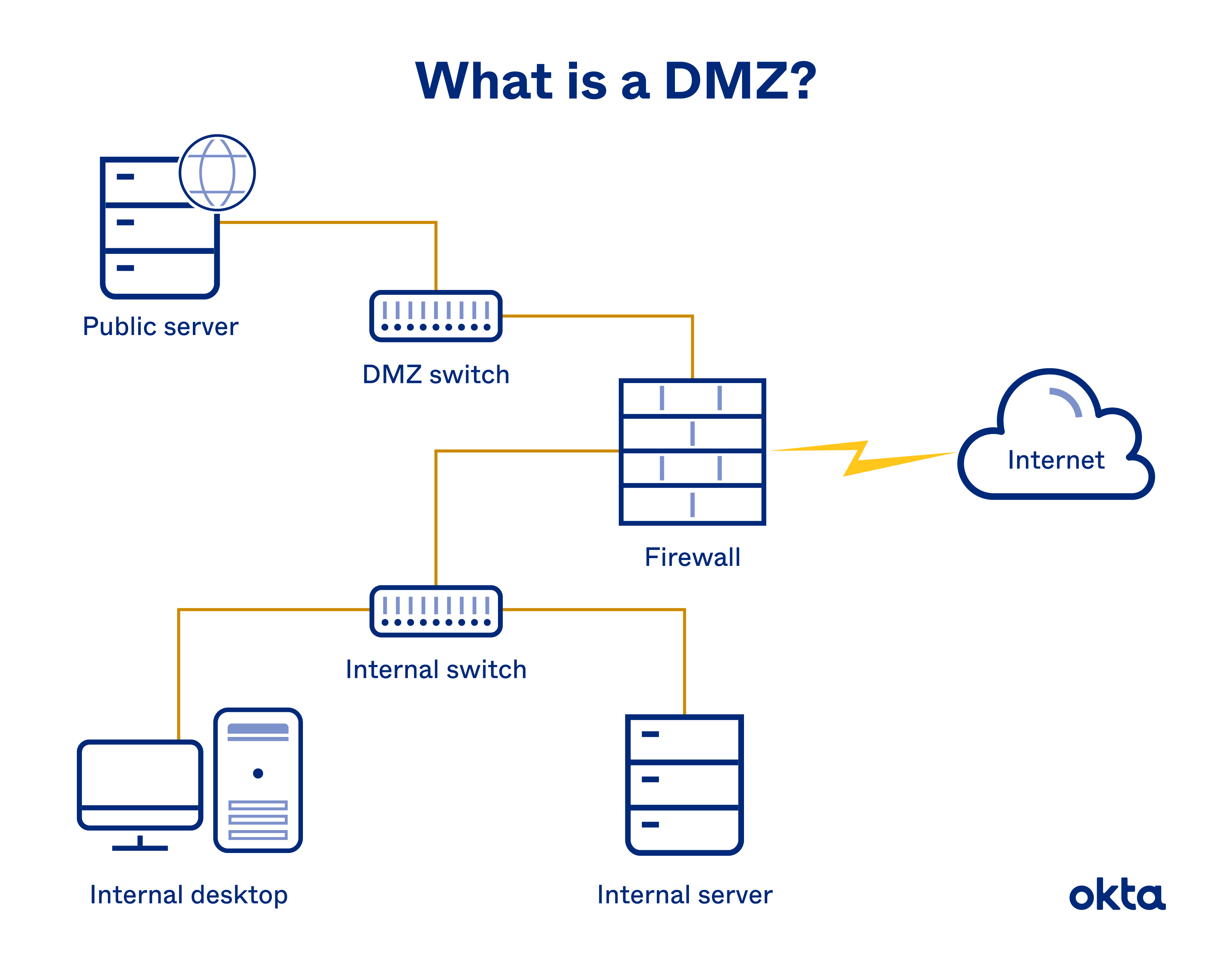
Demilitarized zones or DMZs are isolated network segments partitioned by a physical or logical subnet. Also known as a perimeter network, a DMZ acts as a buffer between a local network and wide area networks (WAN) like the internet. DMZ network frameworks isolate critical systems from other internal networks, while also extending administrative control over the segment.
Also read: Configuration Management | Definition, Importance & Benefits
Why Do I Need a DMZ Network?
Organization networks evolve to meet advancing threat techniques to sensitive data and critical infrastructure. Traditional networks with external-facing components had no separation between publicly accessible segments like email servers, web servers, FTP, DNS, and internal elements like databases, proprietary data, and more. A DMZ allows you to:
- Host, configure, and maintain resources available to external users
- Control access to DMZ network and internal network resources
- Isolate target systems with two layers of firewall protection
Exposure to untrusted networks can pose serious cybersecurity risks. Administrators must isolate the organization’s applications, servers, and systems to mitigate the potential compromise. DMZ networks are one solution to accomplish this.
Administrators can move public-facing segments to the network perimeter and separate sensitive LAN(s) with firewalls. To make a hacker’s job more difficult, organizations can place a second firewall between the pseudo-public DMZ and public networks accessing organization resources.
Also read: Best Database Software & Systems for 2021
How Do DMZ Networks Work?
DMZ networks are proxy networks, filtering and passing data between private and untrusted public networks. Earlier versions of DMZ networks might have had a single firewall separating the externally-facing public domain and the internally protected resources.
Over time, the staple of demilitarized zones became the dual-firewall deployment on both ends of the perimeter network. One firewall sits between internal networks and the DMZ to monitor outgoing traffic, while the other sits between the DMZ and the public network.
Are DMZ Networks Vulnerable to Attack?
For malicious actors seeking to access an organization’s crown jewels, there is a path through the DMZ network. As a public internet user, the hacker can enter the demilitarized zone through a valid resource request. If successful in gaining additional privileges within the perimeter network, the user could garner access to the internal network or compromise the DMZ.
Web application servers connected to internal databases are just one example of how a user could attempt to jump the firewall. With today’s sophisticated tactics, determined actors can linger within DMZs or the internal network while planning the subsequent steps in evading detection and stealing data.
Though DMZ networks were once the solution for addressing data loss prevention (DLP) for web hosting organizations, the proliferation of applications makes it increasingly difficult to defend against east-west network movement. As cybersecurity stakeholders consider alternatives, no recommendation has been louder than moving towards zero trust.
What Is a Zero Trust Network?
A zero trust network is a conceptual framework that gives administrators complete visibility and control over network traffic and resources — and crucially, protects the network’s most sensitive data points. Through a discovery process, organizations identify their most valued digital assets and network segments to build a defensive architecture that prioritizes critical assets.
While the network security strategy of the past looked at the perimeter, endpoint users, and stopping threats from entering the network in the first place, this becomes more difficult by the day. Cloud services, remote work, and the IoT boom are all trends contributing to increasingly complex network perimeters. As the boundary fluctuates, the process to continually defend the network at large becomes more exhausting for administrators.
Also read: Best Server Virtualization Software for 2021
Features of a Zero Trust Network
- Inventory of network segments, resources, and traffic logs, including protect surfaces
- Identity and access management via the authentication of users, devices, and apps
- Strict privilege management for authorized users to prevent lateral movement
- Microsegmentation via network fabric, hypervisor, endpoint outsourcing, or NGFWs
- Robust log management to manage and analyze trusted and untrusted transactions
Zero Trust: Not Just a Buzzword
Since its conceptual roots at Forrester almost a decade ago, zero trust has become the most recognizable buzzword in cybersecurity in the last few years. Though hype can inflate importance, that isn’t the case with zero trust. Organizations implementing ZTNA recognize how beneficial the results are in establishing a sustainable defense posture.
The downside here is zero trust isn’t a concrete, one-size-fits-all product or service. Software developers can provide the needed security tools, and managed service providers can offer guidance for implementation, but making the jump and investment can be a tough decision for administrators.
Also read: Using Zero Trust Security to Protect Applications and Databases
DMZ vs Zero Trust: How Do They Differ?
Both DMZ and zero trust networks aim to protect sensitive data and resources and require some investment into establishing and maintaining the security system. Implementing a demilitarized zone is a longstanding method and, therefore, a far more standardized process than the elusive zero trust deployment.
The increasing complexity of distributed networks, traffic, and endpoints is partly why DMZ networks aren’t strong enough for the modern threat era. Perimeter networks offer a tangible buffer between untrusted users and internal segments. But that’s an entirely different approach from zero trust, which looks and works from the inside out.
Zero trust architectures reside within internal networks and position security controls at specified segment gateways. Whereas earlier networks and even DMZs are vulnerable to insider threats, zero trust is the most robust strategy for combating lateral movement between segments today.
Is DMZ Dead?
It’s easy to assume that zero trust is a superior alternative to DMZ networks, but the two frameworks can work together to provide optimal security to organizations.
Both frameworks offer different benefits to prospective organizations:
- DMZ networks create a hybrid-trust zone and buffer for threat actors
- Zero trust networks create granular policies internally to combat lateral movement
Today, virtualization and containerization make isolating network segments, resources, and components seamless. The need for on-premises web servers continues to dwindle as organizations adopt cloud services that remove the traditional risk of jumping from DMZ to the internal segment.
Also read: On-Premises Infrastructure is Here to Say. Which Workloads Go Where?

